Tag Archives for " Technology "
Artificial Intelligence Provides Great Opportunity for Off-Highway Equipment Industry
David Batcheller of Appareo recently sat down with OEM Off-Highway editor about the potential for Artificial Intelligence (AI) and augmented reality, as well as what challenges and opportunities lie ahead for the heavy equipment industries.
“AI has the potential to make decisions for operators,” says Batcheller. In the off-highway industry, using that capability can help to reduce the amount of training required for operators. Less experienced and well-trained operators can become more effective and more quickly become experts which can help to overcome the current labor shortages construction and other off-highway applications are facing.
You can read the article and watch the full video here: https://www.oemoffhighway.com/trends/video/21723061/ai-provides-great-opportunity-for-offhighway-equipment-industry
https://appareo.com/2021/10/27/artificial-intelligence-provides-great-opportunity-for-off-highway-equipment-industry/
Critical Questions to Ask a Potential New Electronics Supplier
Manufacturers are faced with many different technologies to be considered in the design, manufacture, and deployment of new vehicles. In many circumstances, it isn’t practical for one manufacturer’s engineering group to really understand how to best leverage these technologies to create differentiation that positively separates your brand from the competition. Separation from your competition is important, and that makes the selection of the right supply chain partner an important task.
So how do you evaluate suppliers to find out if they have the right “stuff” to deliver on the differentiation you need? In this post we will outline what you should consider when selecting the right partner.
Demonstrated Capability
Find a supplier you’re excited about and ask about the last time they helped transform a customer’s business through their technology. Even if the technology is not what you are interested in right now, it’s critical to know if they have experience fielding new technological developments, even if in an adjacent industry. Being first to the world with an technology approach to a problem is hard, and you want to work with people who have been down that road before and understand how difficult it is likely to be. Then, you can be more confident they have the will to overcome the unknown obstacles that will come along the way.
Where we’ve seen some of these partnerships break apart in the past is when organizations who have never really moved an industry attempt something audacious, not understanding how difficult it is really going to be. You have to make sure you’ve got a supplier that is going to step up when the going gets tough, because it will.
Make sure that your supplier can explain new and exciting technologies both in a layperson sense and in a highly technical manner. As Einstein once said, if you can’t explain something simply, you don’t understand it. Don’t let acronyms, jargon, and engineering talk convince you of a supplier’s competency. Make sure they can explain the technology in a way the board, your engineers, and your end customer would understand and are convinced by.
Philosophy & Culture
Innovation is hard. To create technology-based differentiation, with the intent of winning market share, innovating with your supplier is going to hurt a little bit. Doing innovation of real marketplace consequence is challenging — it will take longer, cost more, and challenge your business and your supply chain partnership in ways that cannot be anticipated at the outset. That means you need to have a strong alignment and shared philosophy with your supplier at the outset, to make sure your partnership can weather the storm.
So what do you evaluate in the initial conversations with this new supplier to find out if that alignment is really there?
We’re big advocates of bringing business problems to technical supply chain partners on a regular basis, to challenge them to open new, high-value, differentiable opportunities for your business. If you’re being introduced to a new potential supplier and looking to see if you have a fit, ask them about:
1. The most difficult part of a significant development from their business. Ask specifically about the biggest surprise — the real challenge they never saw coming.
- A great potential partner is going to be honest and describe something that really, really sucked. They’re going to use it as an opportunity to highlight their team’s heroics and how they overcame the challenge. Beware of suppliers who cannot be real about facing a challenge. If they’ve never seen it, they’re the wrong people, and if they can’t be honest about it, how are they going to be transparent with you when it becomes really hard during your project?
2. Where they see a specific technology going in the next five years in your industry. Challenge them to defend the opinion.
- You want a supplier that is convicted about your approach and shares your strong opinion about where you are headed. Difficult things take a shared commitment; asking your supplier to defend a shared opinion early, and utilize some devil’s advocacy to test that convocation, is a great way to explore this early.
3. Something that everyone in the industry generally believes to be true about emerging technology that they completely disagree with.
- Great new innovations come with some controversy. The incumbents that are disrupted by the innovation will defend the conventional approach. Test your partner by asking where they disagree with the conventional approach and challenge them to defend it.
Testing Commercial Alignment
Talk early about the investment that both businesses are going to make in fielding a new and exciting solution for the market. There is both a real cost and opportunity cost to each new partnership. You should explore why it is a great fit for both of you, at a high level, and feel comfortable that your supplier’s conviction about that fit is real.
It is critical that the potential relationship and return for both you and your supplier are highly aligned, and testing this early is critical for any highly innovative product launch. When the product is going to be risky and innovative, the deployment will sap a lot of mindshare from your supplier — you want to be sure the reward and opportunity for your supplier is going to hold their attention and motivate the level of effort necessary to overcome any timeline, technology, or cost obstacles.

David Batcheller
President & CBO https://appareo.com/2021/03/29/critical-questions-to-ask-a-potential-new-electronics-supplier/
As a manufacturer, I should really control my data
The world is getting more and more connected. I’m connected to my car, my kid’s watch, and my doorbell. If I was to buy a new airplane, I’d expect to be connected to that too. For engine and airframe manufacturers considering their connected strategy, there are two approaches. In this post, we will go over both of them, but I am personally an advocate of the Open approach.
Open and Closed Approaches
At a really high level, there are two approaches to making airframe and engine connectivity happen: Closed and Open.
The Closed approach is a full connectivity system delivered by one supplier. This includes onboard avionic, a backend/cloud service, and a mobile/web experience. The Closed approach is attractive because it is an “easy button” one-stop-shop for connecting an aircraft. The downside is that you are no longer in control of your data, your customers’ data, and you’re going to rely on the permissions granted by a supplier for information that is increasingly critical to your business. Also, with a Closed approach you are not able to modify or add functionality to the system. As the saying goes, “data is the new oil,” and with this approach, you have given your supplier your mineral rights.
The Open approach is where a supplier brings an open platform connectivity system for an avionic device. This means that you can change the software on the system (either internally or with contract resources). This typically means that you need to develop your own backend/cloud service and mobile/web experience. Undoubtedly, this is harder and requires more effort than a supplier-delivered, turn-key, approach. As they say, nothing worthwhile is ever easy. We will discuss the upside below. With an Open approach, you control your data, how it is used, and how it can direct the path of value-added services that are built off this data. This data is “digital oil” and is incredibly valuable to you in so many ways.
Control of Data
Before discussing data and value propositions, it is important to understand that to achieve these, you must control the data. There are different perspectives on data ownership. Some people believe that the operator/pilot should control the data. Others contend that the ownership of the data should reside with the airframe or engine manufacturers. In any event, your supplier should not own or control your data. It is simply too valuable to have to ask for permission to access, modify, and mine.

Decreased Costs
Access to this data provides opportunities for cost reductions or avoidance of expenses. These cost reductions come in a number of different packages. Having data about the fleet and its operation can lead to value-added services that improve fleet safety, which limits litigation and settlement expenses with a reduction in incidents/accidents. This data can also be used to provide the evidence necessary to negotiate with insurance carriers and provide critical information to manage this growing industry expense. Lastly, the data can be used to understand the circumstances related to warranty claims. This can lead to the avoidance of payment on unjust claims and the improvement of design to eliminate future claims in related areas.
Increased Revenue
Control over the data creates potential for delivery of value-added services to customers, which creates potential for new streams of revenue. Such services can include things like:
1. Web-based analytics that allow for more productive utilization of shared aircraft assets in a fleet environment.
2. Utilization of data to deliver timely parts.
3. Maintenance services to efficiently minimize aircraft downtime.
Interesting opportunities can also emerge in the monetization of third-party, value-added, services through APIs that allow selective access to your data. In these cases, a programmatic interface is created to allow additional companies to access data, at the customer’s request, to provide more niche services at high value. Access to that data can be monetized, with a fee charged to the third party, giving you a portion of their revenue stream without any of the development or maintenance burden of the niche application.
Expansion Potential
Whenever one of our customers really starts to dig into their data, two things emerge. The first is value. The second is more questions that, if answered, are expected to uncover additional exciting business value.
This is where an open platform is also critical. Answering those questions can involve changes to the software on the avionics, changes to the backend architecture to mine/compare/contrast data in different ways, or changes to the mobile experience to better present customer features or track customer behaviors. With an open platform, the cycle of data acquisition, analysis, and value creation becomes an evergreen — but only if you have the control necessary to drive the evolution of your connected ecosystem.
Flexibility
At Appareo we believe you should have the freedom to choose. You should be free to choose which avionic supplier you select for different aircraft platforms. You should be free to choose which mobile devices are compatible with your solution. With an open system, you are free to specify, implement, and manage these choices. With a closed system, you are locked into the offerings and mobile device support from a single supplier. That supplier may be great, but you are also locked into the supplier’s timelines for supporting new generations of connectivity technology (4G, 5G, etc.), as well as the timeliness with which that supplier can offer you access to connectivity services in new countries.
Control of Security
An Open platform doesn’t mean unsecure. Open means having the freedom to impose your cyber rules and requirements on the system, ensuring that your security preferences are embodied in your connected solution. When you own your security you have the comfort of certainty. When you’re working in a closed party system, there are always questions about the security and control of access to your avionics, your data, and your customer’s data. This should be an area you want to control.

Kris Garberg – President, Aviation
https://appareo.com/2021/03/01/as-a-manufacturer-i-should-really-control-my-data/
Maximizing Battery Life In Portable Electronics: What You Need To Know
Now more than ever, the management of battery capacity is a key factor in delivering a positive or negative experience with portable electronic devices, and ultimately the value your customers derive from them. Running out of battery power and losing access to a battery-powered device can result in a range of frustration — from significant inconvenience to full-blown destruction of key business value. In this blog post, we’re going to talk about essential considerations for how battery life is managed in portable electronic devices.
Over the years, Appareo has worked with many different battery chemistries — from alkaline batteries (e.g. “AA” or “AAA” batteries) that we use in common household devices such as remotes and toys, to specialized chemistries like lithium thionyl chloride for extreme environments. Our focus in this blog post is going to be on lithium-ion polymer batteries, the common battery chemistry used for rechargeable cells.
How Electronics Consumers Can Improve Total Battery Life
Tip 1: Keep a battery well charged and charge it between uses, even if (especially if) you didn’t use most of the battery.
The first reason batteries age and hold less charge is due to the number of cycles. What constitutes a “cycle?” There’s no consensus in the battery community, but in general, a cycle is the function of taking a charged battery, consuming some of its energy, and then replacing that energy by recharging the battery. When less of the battery is consumed, it’s less stress on the battery. Therefore, it’s better for you to recharge a battery after consuming a little bit, as compared to draining the battery completely before recharging.
Tip 2: Keep your battery out of hot environments, especially when being stored for longer periods of time.
Another reason batteries permanently lose capacity is due to heat stress. If a battery is exposed to high temps (hotter than 86°F) for extended periods of time, the battery will permanently lose charge. This commonly happens with portable electronic devices that are left in hot cars for hours or days at a time, where high temperatures will stress the battery and destroy its potential.
How Manufacturers Can Improve Total Battery Life
There are reasons that battery life may be diminished that aren’t in the control of the consumer, but instead have to do with the way electronics are specified and implemented. When design engineering a portable electronic device, manufacturers should consider how long customers expect the battery to last, and how much time customers expect to be able to use the device on a charge. One of the ways manufacturers can affect battery performance is by controlling the capacity the battery is operated at. Controlling the capacity involves picking a range that creates the longest battery life, and only operating the battery in that range (e.g. between 25% and 85%). Most batteries will have a longer life in this charge condition than if the battery is operated persistently between 50% and 100% capacity, for example.
A second way manufacturers can have control in this area involves managing the voltage at which the battery is charged. Lowering the charging voltage prevents the battery from getting fully recharged. For example, most batteries are charged at 4.2V. If the charge voltage is lowered to 4.0V, customers may only be able to charge the battery to about 75% of its rated capacity, leaving 25% of the potential battery life on the table. Doing this will increase the number of cycles the battery can withstand by a factor of 2-3 (e.g. from 500 to 1,500 cycles).
Either one, or both, of these approaches will sacrifice total capacity of the battery to improve the life of the battery, and in some applications may be worth the tradeoff.
 Christopher Horne – Director, Electrical and Electronics Design
Christopher Horne – Director, Electrical and Electronics Design
https://www.appareo.com/2021/02/08/maximizing-battery-life-in-portable-electronics-what-you-need-to-know/
Configuring Wake Modes to Maximize Battery Life in Cellular Asset Trackers
Operators want to use their expensive machines (loaders, sprayers, excavators, aircraft, etc.) as much as possible, because at the end of the day, business assets are more of an asset when they’re put to work. When a fleet is distributed over a large area, knowing where equipment is so it can be put to work can be a challenge.
Over the last decade, it has become common for larger or more expensive equipment to be delivered from the original equipment manufacturer (OEM) with a telematics standard. Sometimes it’s a simple position reporting modem, other times there’s a huge volume of operating detail being delivered to the cloud. In any event, it makes it much easier for operators to start tracking a fleet of assets when the equipment comes standard with tracking capability.
The challenge
There are still holes when trying to conduct an efficient operation with a full picture of the fleet. These holes exist because many fleets have equipment that did not come with factory telematics.
For example:
- Tenders, dump trucks, and other Milk Run equipment that create the maximum productivity of a working asset also typically do not have stock telematics
- Specialized equipment produced in lower volumes by smaller OEMs, and therefore not factory-equipped with tracking features
- Towed equipment that is not electrified (e.g. trailers, carts, screens, mowers, balers, tedders, rakes, grinders, chippers, etc.) and as a result have no built-in tracking connectivity
- Expensive attachments that are unpowered
- Older equipment that is in good working order but was delivered before connectivity was standard among major OEMs
Considering these holes, you may only be able to track a portion of the fleet. Even if it’s 75%, it’s not good enough. A project can’t happen if only 75% of the equipment is at the site. That makes these holes important to fill, but it also has to be easy. Operators don’t have the time or the interest to assemble a pile of dissimilar aftermarket technology offerings into a fleet tracking solution — they have a business to run.
The good news
In a previous blog (Understanding 4G LTE Categories) we discussed new kinds of cellular technology that have emerged as a portion of 4G offerings. These technologies, specifically NB-IoT and M1, create opportunities for very rugged and affordable “slap and track” cellular asset trackers. These kinds of trackers can be attached to any piece of equipment, and by using their own battery they can report its location for years.
![]()
This can be an easy fix to the problem, but getting real satisfaction out of these solutions is all about managing the battery life of the unit. Why?
- Many rugged asset trackers are made without replaceable batteries in order to achieve an IP67 or IP69K rating. Although these trackers are cheap, they need to be discarded when the battery is used up.
- Trackers with replaceable batteries lose the “easy fix” appeal once you’re spending time tracking down machines to charge their units or replace batteries. The appeal of this solution is ruined if you can’t leave a machine alone for at least a season — ideally for the life of the machine.
So, how do you use “slap and track” solutions to the maximum benefit of your business? I know people hate this answer, but it depends. As you consider your equipment tracking goals, it’s important to understand battery life and wake modes.
Understanding battery life in cellular asset trackers
Battery life is fixed, meaning you start with a bucket of energy and that is all you get. Therefore, to achieve maximum customer value, the focus needs to be about extending the duration of time that a rugged asset tracker can be used.
To maximize that energy:
- Devices need to be off as much as possible
- When on, devices should sparingly use the components that use a lot of energy (e.g. cellular and GPS)
Device manufacturers have put a bunch of battery management tools into these devices, and the asset tracking ecosystem, to make tracking as easy as possible. It varies by manufacturer, but when a device is advertised to have a 5-year lifetime, that’s typically based on an expectation of a few thousand positional reports over its lifetime. That works out to 1-2 position reports per day for five years. So, while the device’s lifetime is marketed in the form of years, in reality the lifetime is based on the number of positional reports utilized.
Understanding how different wake mode configurations affect battery life
Making the most of the battery management tools should get careful consideration as you deploy trackers. We recommend consulting with your tracking services or hardware supplier to dial this in as early as possible. Devices can typically be configured to report in the following ways (organized from most power hungry to least power hungry):
Periodic continuous reporting
For trackers that are integrated into the machine and connected to vehicle power, this is an easy and inexpensive thing to do. However, most customers with battery powered trackers will not want to use this mode. Having the device report every minute, or even every hour, will consume a lot of battery life.
Wake and report on movement
Many asset tracking devices include an accelerometer. These are great because they use minimal energy and can be used to wake the device when it moves. This is helpful if you want to know when equipment is moving from site to site or when equipment has begun working, for example. Depending on the tracker’s capabilities, it might be possible to set the device to report on movement but then to “snooze” for a period of time (e.g. 4 hours). A word of caution, however: if you can’t snooze its reporting behavior, this feature could run through the battery life quickly.
Wake and report on rest
This is related to the movement feature, but it notices when the device stops moving for a period of time (typically configurable) and then reports the device position. It’s an inverted version of the previous feature with the same benefits and challenges.
Start of day / end of day position reporting
This feature is generally easy to configure, easy to implement, and very friendly for battery life. Simply pick a time of day and have the unit report its position at that time every day. This can give you an overview as to where the equipment was left at the end of the day, giving you an opportunity to dispatch resources effectively at the start of the following workday. When combined cleverly with some of the above features (e.g. report equipment position at 5:00 PM, then report on movement in the event someone moves it after hours), it can be used to give an effective and timely overview of fleet positions while using minimal battery.
Wake on demand
This easy to use feature is very powerful and enabled by the newest generation of cellular technologies. For those of you who want to push your glasses a bit higher on your nose and nerd out with us about how this feature works, we’ll dig deeper in a future blog. For this post, we’ll talk about the capability at a high level so you can understand how to exploit it.
Using a computer or mobile device, you ask the equipment to report its location. This feature sends a message over the cellular network, which is stored in a mailbox of sorts. The device periodically checks that mailbox, using very limited energy, to see if it needs to report in. If there’s a request waiting, it reports its location.
The beauty of this feature is that whenever you need to know the location of an asset, you can have the device report in at the push of a button. The report doesn’t come back in seconds, because typically the device is configured to “check the mailbox” at scheduled intervals in order to minimize energy use. However, even waiting a few minutes to get the devices’ location is MUCH faster than driving from site to site looking for it.
Do you want future connectivity advice, insights, and information delivered to your door? Join our email list, and follow us on LinkedIn.
![]() David Batcheller – President & CBO
David Batcheller – President & CBO
https://www.appareo.com/2020/12/14/configuring-wake-modes-to-maximize-battery-life-in-cellular-asset-trackers/
Top two security issues for connected machines
It is important for our machines to be connected. From industrial asset trackers for inexpensive off-road vehicles to satellite telemetry solutions for business jets, original equipment manufacturers (OEMs) are counting on embedded connectivity solutions to deliver high business value for them and their operators. To deliver this value, these connectivity devices are networked to critical onboard engine, hydraulic, display, and navigation equipment to provide the rich data needed to exploit the business value of the connected tractor, loader, or aircraft.
With all of these interconnections and access to critical machine or aircraft systems, there is an obvious need to ensure that such connections are secure. Security is a confusing and acronym-laden space that can leave buyers uncomfortable or uncertain. To combat this, we’ll focus in on the top two areas that you should have a strategy for:
1. The hardware and software on the device itself
2. Transportation of data from device to cloud
Understanding Keys
First, it’s important to understand the concept of a “key” when discussing security concepts for telematic devices. In a simple sense, information is scrambled using an algorithm, and the key unlocks that information. If you’ve ever used paper cutouts over a page of text or a pinwheel decoder to extract a secret message, you’ve experienced a sort of encryption, or cipher, and a key. There are many different manifestations of encryption and key structure, but the concept of an algorithmic encryption and key to enter/exit that encryption are consistent across these concepts.

In a simple sense you can divide security concerns within a telematic device into hardware and software. You need to be confident that the software on the device is genuine, has not been corrupted by some bad actor, and is not attempting to do anything nefarious. You also need to be sure that the hardware is secure, so the electronics are protecting the data resident on the device (including the secret decoder keys that unlock the encryption the device uses to communicate).
Hardware Security Onboard a Device
There are some spectacular tools available to device manufactures to secure applications and storage onboard telematic controllers. For example, Arm TrustZone allows the device manufacturer to secure certain ranges of memory and flash from snooping and sniffing. This security extends to the ability to secure these ranges from the application software onboard the device itself, so even the application running on the device cannot read that data off the flash and send said data to the cloud.
Why is this important? One example of a security vulnerability is to send a false application update to a device, whose express purpose is not to successfully corrupt/replace the application software, but instead is the first component of a multi-stage attack in which the initial attack’s objective is to steal the encryption keys from the device. In such a situation, the application is falsely deployed to the device and retrieves the keys. Even though it fails to update, the device uses the telematic capability of the device to offboard the keys and enable a subsequent, more dangerous attack. With such hardware security enabled, you would not be able to read the protected memory locations, the false application update would be rejected, and the device would continue on its way.
One example of a security vulnerability is to send a false application update to a device, whose express purpose is not to successfully corrupt/replace the application software, but instead is the first component of a multi-stage attack in which the initial attack’s objective is to steal the encryption keys from the device. In such a situation, the application is falsely deployed to the device and retrieves the keys. Even though it fails to update, the device uses the telematic capability of the device to offboard the keys and enable a subsequent, more dangerous attack. With such hardware security enabled, you would not be able to read the protected memory locations, the false application update would be rejected, and the device would continue on its way.
A different approach to hardware security is through the utilization of trusted platform modules (TPM). In this case the keys are stored entirely within a different, secure, integrated circuit that is separate from the core product’s processor/memory, and the keys never leave the TPM. Trusted platform modules can also play a role in secure boot as a special sequence initialized only by the correct software, in the correct order, to “unlock” the TPM.
What level of hardware security is appropriate for your application will vary, based on your deployment’s risk profile, the capabilities of your device, and the technologies supported by your server-side infrastructure. What is important is that some consideration is made for securing your device at the hardware level, and that you and your device manufacturing partner are united in your approach to telematic hardware security.
Software Security Onboard a Device
With good hardware security and key storage in place, the updating of the application onboard the device itself can be secured, regardless of whether that update is through firmware updated over the air, or by connecting physically to a device. This security ensures that no bad actor can replace or modify the software onboard your device. This security is achieved by having the application signed with a secret/private key. The signing of this application ensures that the device can verify that the software is genuine, or trusted, before allowing the software to be run on the device.

When transmitting data, there is the protocol being used to transmit data and the method of security that is applied to that protocol. Typically the security and protocol are separate considerations. So whether you are using a popular telematic protocol like MQTT or a UDP IP based protocol like CoAP, there are methods by which that data can be encrypted in its transfer from the device to the Internet, where it then transits to the server. In this sense, most typical security concerns are focused on the data’s pathway through the Internet on its way to its server location more so than the radiation of the data in free space from the device’s antenna.
In the world of data encryption there are two high-level concepts that are important to understand: symmetric encryption and asymmetric communication of data.
Symmetric Encryption
 Symmetric encryption is when you open a “secure channel.” If you think about the President of the United States and the red phone for secure calls, that is a very good analogy for symmetric encryption. This is a secure two-way channel for communication. For applications where the receiver and sender are in the same organization, or the device and end-point receiving the data are designed by the same company, this system is commonly and effectively employed. This technology is commonly used in applications like banking transactions and data at rest (not in transit from one server to another).
Symmetric encryption is when you open a “secure channel.” If you think about the President of the United States and the red phone for secure calls, that is a very good analogy for symmetric encryption. This is a secure two-way channel for communication. For applications where the receiver and sender are in the same organization, or the device and end-point receiving the data are designed by the same company, this system is commonly and effectively employed. This technology is commonly used in applications like banking transactions and data at rest (not in transit from one server to another).
Asymmetric Encryption
In this method of security, there is a public key that can be used to encrypt data to be sent to a receiver, but a secret key that is possessed by the receiver is the only way to decrypt the data. Where different organizations are communicating with one another, or when several organizations might be contributing data to a common dataset, such a security methodology is very effectively used. Asymmetric encryption is commonly used in applications like digital signatures and is a feature of transport layer security (TLS) or secure socket layer (SSL) communications.
One of the shortcomings of asymmetric encryption is that it is much slower to implement and use on devices because the encryption algorithms are complex and require more computational power to run. This is unfortunate for embedded devices where processing capabilities are often a significant limitation. Although symmetric encryption doesn’t require as much computational power, it requires that secret keys be effectively distributed and maintained, which is a separate challenge.
Hybrid Approach
With consideration for the challenges above, it is common in messaging and telematic applications to employ a hybrid model. With this model, an asymmetric message is used to open a secure channel and exchange keys to begin the session between the client and the host, so that session can subsequently be done with safe, secure, lower-overhead symmetric encryption. For example, the client can use a public key to send a message to a host describing all of the information the host needs to connect back to the client using symmetric encryption (a shared secret key).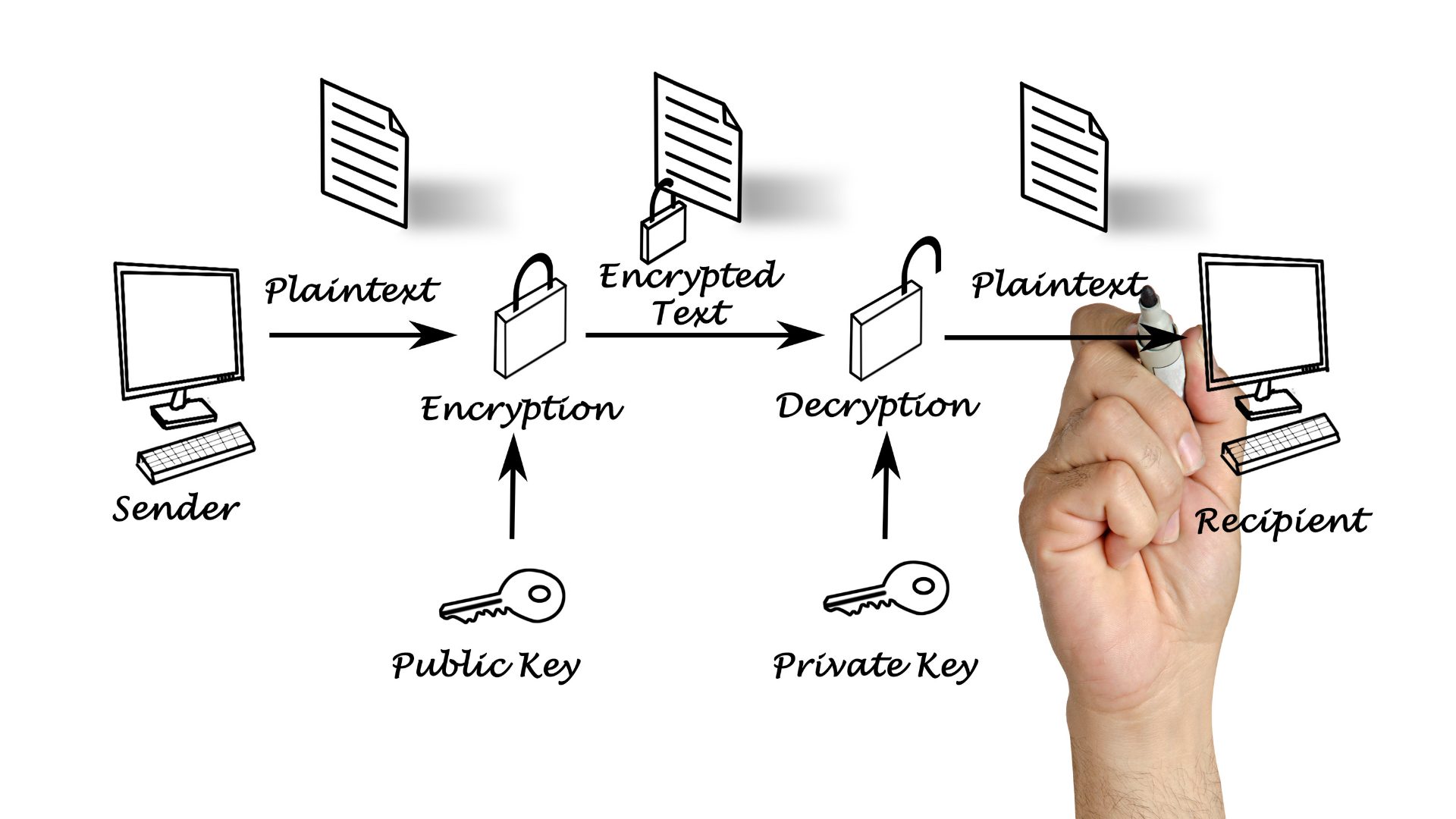
No One-Size-Fits-All Approach
A good security strategy is a collaborative effort between the device manufacturer and the OEM. For example, in a simple asset tracking use case with a battery powered asset tracker that needs to optimize battery life for a longer duration, the asymmetric public key transfer could use 6k of data in the process of sending a one-time 500-byte message. That means that throughout the life of the device, more than 90% of the precious battery life the device is trying to optimize for would be consumed securing the device’s messages. In such cases, like inexpensive IoT sensors feeding asset tracking or environmental intelligence to machinery management systems, the costs in battery life and data transmission may necessitate other approaches to message security.
In a future blog article we’ll cover how a device manufacturer, in collaboration with the cellular or satellite carrier, can be creative in the manner that data is received off the device at the network infrastructure to keep that data off the internet and further contribute to a security solution. Approaches like this can be of considerable assistance when combatting power/data budgets for use cases like the above IoT sensor.
Summary
When considering your connected vehicle deployment, ensure you and your device manufacturer have hardware level key security, signed certificates for software deployment, and a right-sized strategy for encryption of communication to/from the device.
 David Batcheller – President & CBO
David Batcheller – President & CBO
https://www.appareo.com/2020/12/07/top-two-security-issues-for-connected-machines/
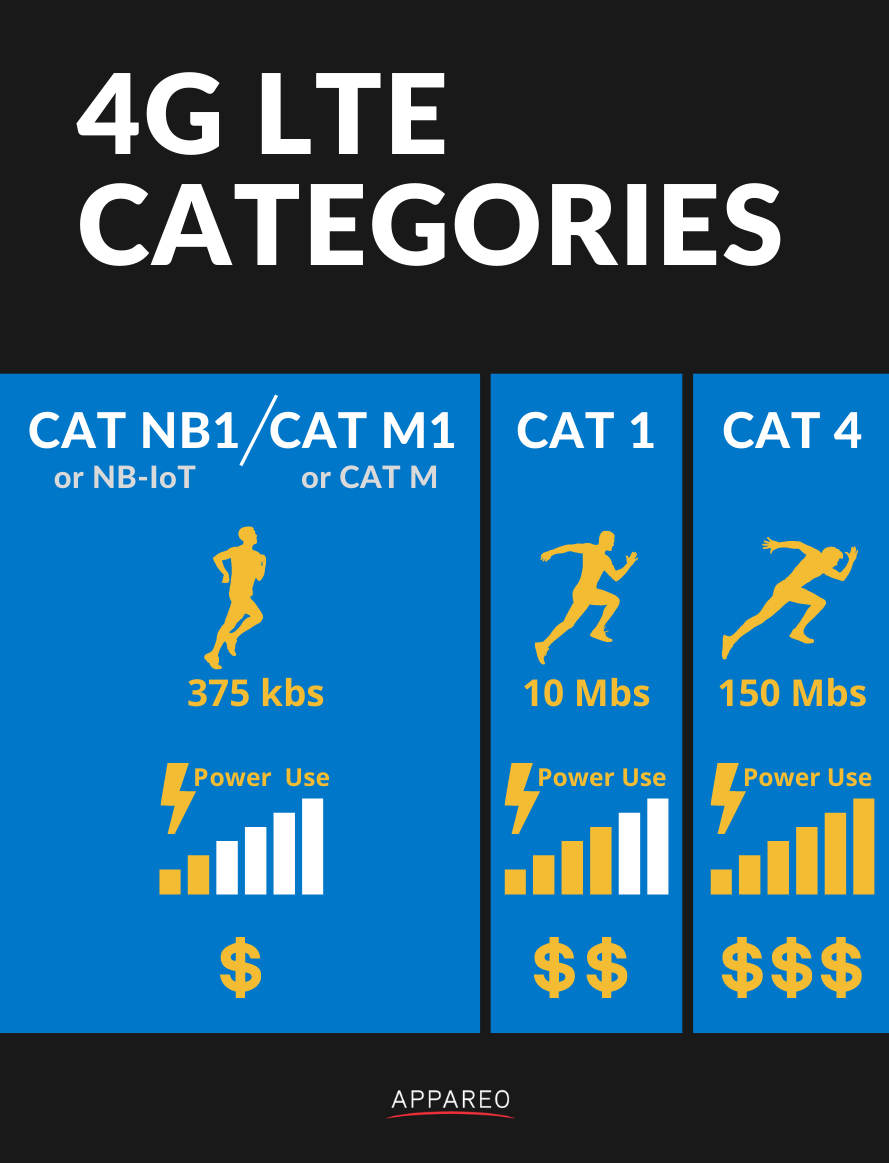
Understanding 4G LTE Categories
LTE consists of a range of different categories of modem, which can be integrated into telematic devices. These different categories include:
-
- CAT NB1 (also referred to as NB-IoT)
- CAT M1 (also referred to as CAT M)
- CAT 1
- CAT 4
In general, as you progress down the list above, the power consumption, throughput, and price of the devices increases (all considerably). When comparing specifications and capabilities of different telematic devices, it can be difficult to know what is the right level of capability for your cellular data transfer needs. This post will provide a brief summary and application-level insight to this area of potential confusion when specifying or purchasing telematic products.
NB-IoT and M1
Although these newer, low-energy cellular technologies are grouped together, they are not exactly the same thing. Most hardware that supports one also supports the other, so you can prototypically get both capabilities in a single package. This is new and cool, and will continue to grow in things it can accomplish within the geographies where it can be deployed.
Although you’ll hear NB-IoT and M1 discussed in the context of vending machines, pollution monitors, electric meters, and wearables, these technologies absolutely have a role to play in mobile vehicles and equipment. Here is what’s great about both NB-IoT and M1:
- Very low power
- Provide superior range over CAT 1 and CAT 4 modems (our testing has shown that NB-IoT and M1 devices frequently have cellular connectivity in areas where cell phones do not)
- Lowest cost of any cellular components or data plans
- Deploys using existing cellular infrastructure, so lots of new support is expected to come online
- Secure
As my mother always told me growing up, nothing is free. There’s a trade-off for the lower power consumption, lower price, and improved range of the NB-IoT and M1 technologies. Here’s what you spend to get that goodness:
- Lower data rate (~375 kbs)
- Higher latency for wake-up applications
If you have a few sensor parameters, or a couple of buses of CAN data, to send on M1 is a great technology for mobile applications.
CAT 1
This is the bread and butter of telematic connectivity technologies. LTE CAT 1 is capable of supporting feature-rich telematic products with enough throughput to support streaming meaningful amounts of data while vehicles are on the go. The maturity of the technology makes it broadly available in a large number of geographies, with mature modem hardware and firmware support and a full-featured build-out of carrier capabilities. This technology is a little more expensive than NB-IoT and M1, but has the following advantages over those technologies:
- Higher data streaming throughput (up to 10 Mbs)
- Lower latency for wake-up applications
- Broader global coverage
If you need to deploy a solution broadly for mobile equipment (touching dozens of countries), need to offload a fairly large amount of machine data in a hurry, or require support for streaming video or other data-intensive content, then CAT 1 is going to be the way to go for your application.
CAT 4
LTE CAT 4 modems can absolutely scream data. These modems can hit 150 Mbs, more than ten times the throughput of their CAT 1 counterparts. They are also complex, expensive, and power hungry. These modules are typically reserved for spaces like the handset market. Unless you need to aggregate a lot of data from a lot of machines, or provide streaming services to a large number of passengers onboard a vehicle, it is unlikely that the cost or complexity of this technology will be appropriate for your mobile application.
 David Batcheller – President & CBO
David Batcheller – President & CBO
https://www.appareo.com/2020/11/09/understanding-4g-lte-categories/
Choosing the Bluetooth That’s Right For You
Since the introduction of Bluetooth Low Energy (BLE) in Bluetooth 4.0, there are now four technologies used under Bluetooth 4.0 and later revisions. Although the history of naming these technologies has led to much confusion, the generally accepted names are Bluetooth Classic and Bluetooth Low Energy. Bluetooth Classic represents the BR, EDR, and HS (AMP) technologies, while Bluetooth LE represents the LE technology.
Bluetooth Classic devices are typically used in applications requiring streaming of data, such as audio. The physical layer and protocol of BR/EDR make socket-like streaming of data easy to accomplish. Rates of these data streams may be around 2-3 Mbps. Bluetooth Low Energy brings about some great features beyond low energy operation, such as one-to-many and many-to-many communications, as well as connectionless services. BLE is often used for data transmission, location services, and device network applications. These interactions operate much more like a shared database of characteristics through the use of a Generic Attribute Profile (GATT). Most mobile devices such as phones, tablets, and computers support both Bluetooth Classic and Low Energy; however, many devices use one or the other.
Bluetooth Low Energy brings about some great features beyond low energy operation, such as one-to-many and many-to-many communications, as well as connectionless services. BLE is often used for data transmission, location services, and device network applications. These interactions operate much more like a shared database of characteristics through the use of a Generic Attribute Profile (GATT). Most mobile devices such as phones, tablets, and computers support both Bluetooth Classic and Low Energy; however, many devices use one or the other.
Due to the differences in the physical layer modulation and demodulation, BLE cannot talk with Bluetooth Classic and vice versa. Similarly a BLE device cannot use Bluetooth Classic network and transport protocols when talking to a dual mode Bluetooth device. This is critically important for machinery manufacturers because although Bluetooth devices can typically communicate over a local area network to tablets and phones reliably, if you are going to use Bluetooth to communicate between machines and attachments, or between machine ECUs, you’ll need to select a protocol for the network of devices you’re managing.
- BLE can manage the data rates necessary to transfer typica data loads from mobile equipment busses (e.g. CAN buses running J1939)
- Bluetooth Classic can handle a lot more data
- Bluetooth Classic supports mobile devices tethering to telematic gateways or control units onboard machines and letting one device use the other’s data plan
- Bluetooth Classic is much more energy intensive than BLE, so if you have a battery-powered application BLE is the way to go
In summary, if you have a network demand for a fairly large amount of data, and you have access to vehicle power (or battery life management is not a concern), Bluetooth Classic is a good way to go. If you’re a battery-powered application or do not require transfer of significant volumes of data, BLE provides attractive networking flexibility, low power, and a low price.
 Michael Hoffman – Sales Manager, Land Mobile
Michael Hoffman – Sales Manager, Land Mobile
https://www.appareo.com/2020/11/02/choosing-the-bluetooth-thats-right-for-you/
That radio interference might be coming from your cheap USB charger
In modern vehicles, people are more dependent than ever on the presence of a phone or tablet. Most new vehicles come with some sort of USB charging port that may even include USB communication to an in-vehicle infotainment system, allowing for streaming video, representation of CarPlay mapping on the vehicle display, etc. As consumers, we’re now accustomed to getting into a vehicle, plugging in our phone, and having that phone seamlessly connect and work with our vehicles.
But what if you don’t have a newer vehicle? What if your car, aircraft, RV, truck, or tractor was built before USB integration was a common customer expectation?
When shopping for a USB charging adapter you encounter a shockingly wide array of prices for such devices. Many options are available at discount stores or online for as little as $2.00.


The Audi plug meets automotive standards. The other plugs do not.
That means that the Audi charger has been rigorously testing against standards from both regulators and the vehicle manufacturer themselves. The cheap adapters have an ambiguous level of testing and are self certified by the manufacturer (with no regulator or manufacturer oversight).
So what? For automobiles in which USB charging ports are integrated by the manufacturer, they are tested against automotive standards. These standards ensure the devices are fit for the environment and will produce a high-quality customer experience. For example, it is inconceivable that plugging a phone or tablet into the manufacturer’s USB port would cause interface on AM, FM, or two-way radios. Plugging in a device and getting a bunch of static on the FM radio or completely losing two-way radio communication is intolerable.
For automobiles in which USB charging ports are integrated by the manufacturer, they are tested against automotive standards. These standards ensure the devices are fit for the environment and will produce a high-quality customer experience. For example, it is inconceivable that plugging a phone or tablet into the manufacturer’s USB port would cause interface on AM, FM, or two-way radios. Plugging in a device and getting a bunch of static on the FM radio or completely losing two-way radio communication is intolerable.
This is, however, a common occurrence when using charging devices that are not designed for automotive use. A lot of these chargers carry FCC/CE marks, look safe and legit, but ultimately damage your ability to receive and transmit radio communications. This could be as benign as negatively impacting your ability to receive an AM radio station, or as painful and inconvenient as knocking out two-way radio communication completely — especially if that is your aircraft VHF comm.

What do I do about it?
Not all chargers are created equally. There are absolutely some high quality products available through online retailers that won’t cause radio noise. Unfortunately there’s really not much one can do to qualify such a charger when shopping, and the only practical way for pilots to sort through them is to buy them, put them in the aircraft, and see what happens. Many of these chargers will cause radio noise, and that noise will vary from slightly inconvenient to completely unmanageable.
Here are a couple of things to take into consideration when making that choice for your aircraft:
- USB charging technology changes VERY quickly. Just because you bought a charger from a specific brand and it worked, that does not mean that going back to the same supplier next time will provide a product that provides clean power without radio noise. This is because consumer devices are not governed by the same kind of engineering change control and certification practices as products that are regulated by folks like the FAA, or closely monitored by aircraft/vehicle OEMs with good design change control. A lot of consumer devices will roll fast with changes to new technology but repackage in the same tooling — therefore, buying what appears to be the same device might all of a sudden produce lots of interference.
- Vibration activity in aircraft and cars is very different. A lot of consumer-style USB chargers are generally designed in a manner that will be friendly for an on-road automotive experience. It’s a much different environment in the ‘74 PA-28 or M20B that you fly around on the weekends. Aircraft vibratory loads can be rough on devices that are not designed for them, so you might burn through cheaper chargers not designed for the environment rather quickly.
If you really need the radio, and to power a device in the aircraft during flight, you should make sure you can do both with a lot of confidence and use a manufacturer-provided solution (in a new aircraft or service part), or purchase a certified charger that you know is going to work and deliver a consistent experience if it is ever replaced.
Then you’ll absolutely have a charging solution that will allow you to aviate, navigate, and communicate without worrying about losing that last word along the way.
Video examples of radio interference
Check out this experiment after he experienced interference in his RV:
For a deeper dive, watch this video from Kenwood (a radio company). They produced a demonstration with a two-way radio, which is a low-frequency radio (typically between 151 and 154 MHz) that operates in bands similar to those used in aircraft.
 David Batcheller – President & CBO
David Batcheller – President & CBO
https://www.appareo.com/2020/10/12/that-radio-interference-might-be-coming-from-your-cheap-usb-charger/
What’s the difference between SIM and eSIM?
Connectivity technologies are confusing for people, and the industry is loaded with perplexing acronyms and buzzwords.
One of the most recent areas commonly fostering misconceptions is the difference between SIMs and eSIMs. This article is going to break it down in way that will hopefully help to inform your connectivity conversations.
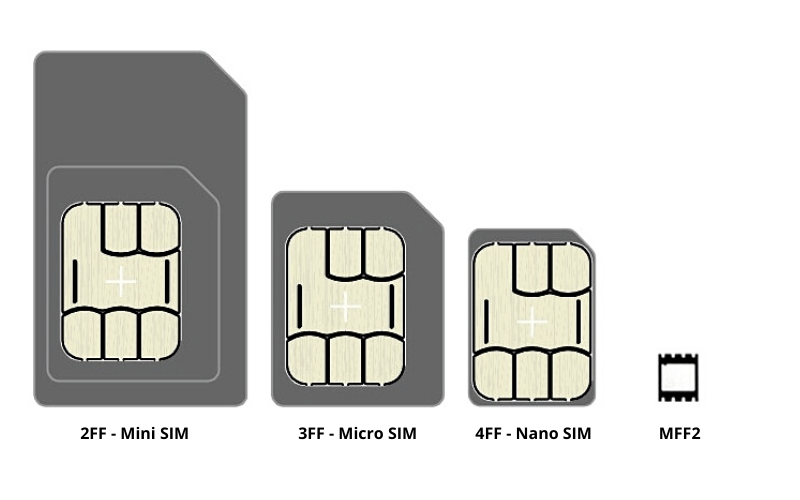
Understanding SIMs The abbreviation SIM means “Subscriber Identity Module” and the devices were originally created to identify which subscriber is associated with a phone. Most people have a specific physical impression of a SIM, which is a little plastic card that we slide into a phone. In fact, there are a number of different physical manifestations of what you would know as a SIM card.
The abbreviation SIM means “Subscriber Identity Module” and the devices were originally created to identify which subscriber is associated with a phone. Most people have a specific physical impression of a SIM, which is a little plastic card that we slide into a phone. In fact, there are a number of different physical manifestations of what you would know as a SIM card.
The industry has different media on which a subscriber for a device can be identified. In general, manufacturers of rugged connectivity equipment strongly prefer and heavily leverage the MFF2 (M2M form factor). This is also sometimes referred to as a Machine Identification Module, or “MIM.” The reason manufacturers prefer these MFF2 units is because the vibratory specifications for aircraft and off-highway equipment are very unfriendly to SIM cards like the 3FF. During rigorous vibration tests, the shaking of the SIM card against its cage (which creates a phenomenon called fretting corrosion) wears through the very thin metal deposited on the plastic and destroys the card, resulting in the cellular function to stop working. Not cool.
eSIM vs SIM
Regardless of whether or not you have a 2FF, 3FF, 4FF, or MFF2 SIM/MIM, that hardware is really just a carrier for the UICC (universal integrated circuit card). This UICC is a read-only network profile. In other words, the device manufacturer will get a pile of chips (in any of the hardware manifestations shown above) that are pre-loaded with keys that cannot be changed during, or after, device manufacture.
Recently, it has become possible to purchase hardware that contains an eUICC (embedded universal integrated circuit card). This change means that instead of having a read-only network key on the SIM/MIMs that the manufacturers receive, this hardware can now be programmable and can host keys from multiple carriers on a single SIM/MIM. Some people initially think “great, I can tell AT&T to get lost and just program my unit over the air to work on Verizon whenever I want.” Unfortunately that isn’t true. Although that would be a great capability and introduce helpful flexibility for a lot of customers in many applications, you simply cannot do that today with an eUICC.
However, this is still really cool for manufacturers.
Here is why you should be excited about eSIM capabilities. Device manufacturers will often work with a carrier partner (e.g. AT&T, KPN, Rodgers, T-Mobile, Verizon, Vodafone, etc.) to certify a device with a specific carrier. Then, behind that carrier are dozens of local networks that will support these devices.
What the eSIM allows people to do is have multiple network profiles for local carriers on a single product, and update those over the air. When a vehicle travels from geography to another while using the same carrier, your device manufacturer can update the device to provision it for the local network, without changing a SIM. This is really powerful for getting products into geographies where cellular plan and regulatory constraints have historically driven a multitude of additional device SKUs and given manufacturers significant headaches managing equipment export — or equipment travel from one geography from another.
Some examples:


For equipment manufacturers, eSIMs are going to be a powerful tool for simplifying connectivity of a fleet while minimizing the burden on the manufacturer and reducing the number of device SKUs required to achieve truly global connectivity.
 David Batcheller – President & CBO
David Batcheller – President & CBO
https://www.appareo.com/2020/10/08/whats-the-difference-between-sim-and-esim/